Description
- Substitution Cipher Solver Tool
- Cipher Solver Tool
- Cipher Solving Tools
- Cipher Solver Tools Download
- Substitution Cipher Solver Tool
- Substitution Cipher Solver Tool
The Solitaire cipher is a substitution cipher. Each letter is replaced by another letter a certain number of steps to the right of it in the alphabet. The cipher uses a pack of cards to generate a sequence of numbers. It generates one number for each letter to be enciphered. The numbers are called keystream numbers and the whole sequence of them the keystream. The numbers govern the replacement of the letters. The first number governs the replacement of the first letter, the second number governs the replacement of the second letter, and so on. Each number represents the number of steps that you must take to the right of a letter to reach its replacement. Sometimes you take enough steps to reach the end of the alphabet. Whenever this happens, the next step is to the beginning of the alphabet.
The cipher uses an ordinary pack of 52 playing cards and 2 jokers. Each card is associated with a number:
| A | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | J | Q | K | |
| Clubs | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Diamonds | 14 | 15 | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| Hearts | 27 | 28 | 29 | 30 | 31 | 32 | 33 | 34 | 35 | 36 | 37 | 38 | 39 |
| Spades | 40 | 41 | 42 | 43 | 44 | 45 | 46 | 47 | 48 | 49 | 50 | 51 | 52 |

The two jokers are both associated with the number 53.
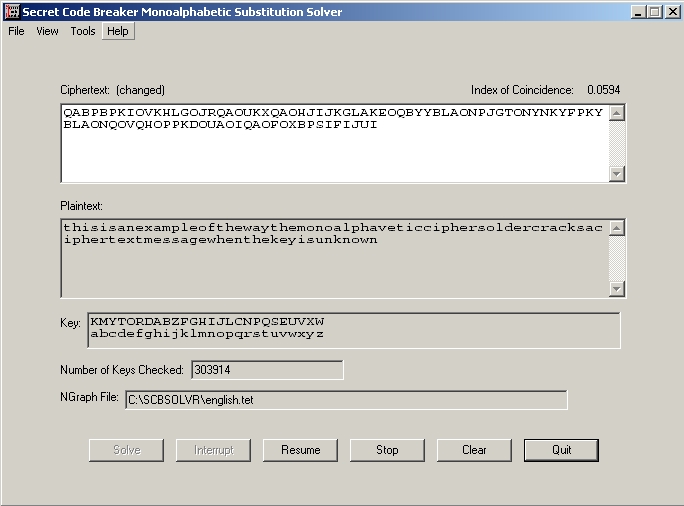
Substitution Cipher Solver Tool
ACA Convention Registration. Vote On ACA's New Officers. ACA Prior Conventions. The Cryptogram: Sample Issue.
(The following rules give you the number for each card. For a joker, the number is 53. For a club, take the value of the card. For a diamond, add 13 to the value of the card. For a heart, add 26. For a spade, add 39. The value of an ace is 1. The values of the Jack, Queen, and King are 11, 12, and 13. For every other card, the value is the number printed on the card.)
- The Rot13 cipher, A1Z26 cipher, morse code, and affine cipher, while an artifact of the machine age, are similarly trivial to solve. From there you move to a full monoalphabetic cipher, with a more complex monoalphabetic substitution system to jumble the secret message. Modern cryptogram puzzles are based around a monoalphabetic substitution.
- Polybius square cipher – Encrypt and decrypt online. The Polybius square or Polybius checkerboard is a method for fractionating plaintext characters so that they can be represented by a smaller set of symbols. Each letter is represented by its coordinates in the grid. Variant Beaufort cipher Base64 to binary Base32.
- Cipher Tools Let's say that you need to send your friend a message, but you don't want another person to know what it is. You can use a full-blown encryption tool, such as PGP. If the message isn't that important or if it is intended to be decrypted by hand, you should use a simpler tool.

The jokers must be different. Call one of them the 'A' joker, and the other one the 'B' joker.
There are 5 steps to generate each keystream number:
Find the A joker. Move it one card down. (In other words, swap it with the card just beneath it.) If it is at the bottom of the pack, then put it just below the top card:
Before 1 2 3 4 A 5 6 7 8 9 B 10 11 12 13 After 1 2 3 4 5 A 6 7 8 9 B 10 11 12 13 Before 1 2 3 4 5 6 7 8 9 B 10 11 12 13 A After 1 A 2 3 4 5 6 7 8 9 B 10 11 12 13 (The diagram shows a reduced pack with just the 13 clubs and the two jokers. But it illustrates the principle.)
Find the B joker. Move it two cards down. If it is just above the bottom card, then put it just below the top card. If it is the last card in the pack, then put it just below the second card:
Before 1 2 3 4 A 5 6 7 8 9 B 10 11 12 13 After 1 2 3 4 A 5 6 7 8 9 10 11 B 12 13 Before 1 2 3 4 A 5 6 7 8 9 10 11 12 B 13 After 1 B 2 3 4 A 5 6 7 8 9 10 11 12 13 Before 1 2 3 4 A 5 6 7 8 9 10 11 12 13 B After 1 2 B 3 4 A 5 6 7 8 9 10 11 12 13 Do a triple cut, as follows. Divide the pack into three parts: the top part, which is all the cards above the top joker (whichever one that happens to be); the middle part, which is all the cards between the two jokers, including the jokers; and the bottom part, which is all the cards below the bottom joker. Swap the top part with the bottom part. Do not worry if either part is empty:
Before 1 2 A 3 4 5 6 7 8 9 B 10 11 12 13 After 10 11 12 13 A 3 4 5 6 7 8 9 B 1 2 Before 1 2 3 4 B 5 6 7 8 9 10 11 12 13 A After B 5 6 7 8 9 10 11 12 13 A 1 2 3 4 Do a count cut, as follows. Look at the bottom card. Work out the number that it is associated with. Take that number of cards from the top of the pack and place them just above the bottom card. If the bottom card is a joker, then do nothing:
Before 5 6 7 8 9 A 10 11 12 13 1 B 2 3 4 After 9 A 10 11 12 13 1 B 2 3 5 6 7 8 4 Before 1 2 3 A 4 5 6 7 8 9 10 11 12 13 B After 1 2 3 A 4 5 6 7 8 9 10 11 12 13 B Find the output card, as follows. Look at the top card. Work out the number that it is associated with. Count that many cards further into the pack. The card that you reach is the output card. If the top card is a joker, then the output card is the bottom card. Do not move any of the cards:
Before 3 4 5 6 A B 7 8 9 10 11 12 13 1 2 After 3 4 5 6 A B 7 8 9 10 11 12 13 1 2 Before A 2 3 4 5 6 7 8 B 9 10 11 12 13 1 After A 2 3 4 5 6 7 8 B 9 10 11 12 13 1 Unless the output card is a joker, work out the number that is associated with it. This is the next keystream number. If the output card is a joker, then repeat steps 1–5 until they produce a card which is not a joker.
To generate a whole keystream, repeat steps 1–5 until you have enough numbers. It is necessary to keep going until the keystream is as long as the plaintext.
The Solitaire cipher resembles the Vignère cipher. The Vignère cipher is a polyalphabetic substitution cipher. For each plaintext letter, it uses a letter in a keyword to select one of the 26 possible Caesar shift alphabets. Then it uses this alphabet to encipher the letter. But enciphering a letter with a Caesar shift alphabet is equivalent to finding a replacement for the letter by stepping a fixed number of places away from it in the alphabet. Hence the Vignère cipher uses the letters in a keyword in the same way that the Solitaire cipher uses the numbers in a keystream.
There are two main differences between the ciphers. Firstly, the key used in a Vignère cipher is usually a recognisable word or phrase. The keystream used in a Solitaire cipher is not. Secondly, the key used in a Vignère cipher is usually much shorter than the text to be enciphered. This means that each letter in the keyword has to be used to encipher many letters in the plaintext. Moreover, these letters are a fixed distance apart. It follows the number of steps taken in the alphabet to encipher successive letters in the plaintext follows a repeating pattern. With a Solitaire cipher, there is no repeating pattern.
Example
Suppose that you wanted to encipher the text
the moment echo saw narcissus she was in love. she followed him like a starving wolf following a stag too strong to be tackled.
The first step is to choose an initial order for the pack of cards. There are several ways to do this. A standard procedure is the following. You begin with the cards in their natural order (1, 2, 3, 4, …, 51, 52, A, B). Then you use a keyword to shuffle the cards. Each letter in the keyword governs a single round of shuffling. There are 5 steps in each round. The first 4 steps are the ones used to generate keystream numbers. The fifth one is different:
Find the A joker and move it 1 card down.
Find the B joker and move it 2 cards down.
Do a triple cut.
Do a count cut, based on the bottom card in the pack.
Do another count cut, as follows. Work out the position of the current keyword letter within the alphabet:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 Then take this number of cards from the top of the pack and place them just above the bottom card.
Suppose that we use the keyword
SOLITAIRE
The cards begin in their natural order:
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B |
The first round of shuffling, using the letter 'S', causes the following changes:
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B |
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | B | A |
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | B | A |
| 1 | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A |
| 1 | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A |
| B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | 1 |
Cipher Solver Tool
| B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | 1 |
| 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 1 |
| 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 1 |
| 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 1 |
(The letter 'S' is the 19th letter in the alphabet. That is why, in step 5, 19 cards are moved.)
So the cards end up in this order:
| 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 1 |
After the second round of shuffling, which uses the letter 'O', the cards end up in this order:
Cipher Solving Tools
| 17 | 18 | 19 | 20 | 1 | A | 2 | B | 21 | 22 | … | 50 | 51 | 3 | 4 | … | 15 | 16 | 52 |
Cipher Solver Tools Download
After all 9 rounds of shuffling, this is the order of the cards:
49 50 51 3 4 5 6 7 8 18 11 12 13 14 17 52 19 37 A 44 45 27 28 15 16 9 10 B 20 1 23 24 25 26 22 29 30 31 32 33 34 35 36 2 39 40 41 42 43 21 46 47 48 38
The two jokers are both associated with the number 53.
Substitution Cipher Solver Tool
ACA Convention Registration. Vote On ACA's New Officers. ACA Prior Conventions. The Cryptogram: Sample Issue.
(The following rules give you the number for each card. For a joker, the number is 53. For a club, take the value of the card. For a diamond, add 13 to the value of the card. For a heart, add 26. For a spade, add 39. The value of an ace is 1. The values of the Jack, Queen, and King are 11, 12, and 13. For every other card, the value is the number printed on the card.)
- The Rot13 cipher, A1Z26 cipher, morse code, and affine cipher, while an artifact of the machine age, are similarly trivial to solve. From there you move to a full monoalphabetic cipher, with a more complex monoalphabetic substitution system to jumble the secret message. Modern cryptogram puzzles are based around a monoalphabetic substitution.
- Polybius square cipher – Encrypt and decrypt online. The Polybius square or Polybius checkerboard is a method for fractionating plaintext characters so that they can be represented by a smaller set of symbols. Each letter is represented by its coordinates in the grid. Variant Beaufort cipher Base64 to binary Base32.
- Cipher Tools Let's say that you need to send your friend a message, but you don't want another person to know what it is. You can use a full-blown encryption tool, such as PGP. If the message isn't that important or if it is intended to be decrypted by hand, you should use a simpler tool.
The jokers must be different. Call one of them the 'A' joker, and the other one the 'B' joker.
There are 5 steps to generate each keystream number:
Find the A joker. Move it one card down. (In other words, swap it with the card just beneath it.) If it is at the bottom of the pack, then put it just below the top card:
Before 1 2 3 4 A 5 6 7 8 9 B 10 11 12 13 After 1 2 3 4 5 A 6 7 8 9 B 10 11 12 13 Before 1 2 3 4 5 6 7 8 9 B 10 11 12 13 A After 1 A 2 3 4 5 6 7 8 9 B 10 11 12 13 (The diagram shows a reduced pack with just the 13 clubs and the two jokers. But it illustrates the principle.)
Find the B joker. Move it two cards down. If it is just above the bottom card, then put it just below the top card. If it is the last card in the pack, then put it just below the second card:
Before 1 2 3 4 A 5 6 7 8 9 B 10 11 12 13 After 1 2 3 4 A 5 6 7 8 9 10 11 B 12 13 Before 1 2 3 4 A 5 6 7 8 9 10 11 12 B 13 After 1 B 2 3 4 A 5 6 7 8 9 10 11 12 13 Before 1 2 3 4 A 5 6 7 8 9 10 11 12 13 B After 1 2 B 3 4 A 5 6 7 8 9 10 11 12 13 Do a triple cut, as follows. Divide the pack into three parts: the top part, which is all the cards above the top joker (whichever one that happens to be); the middle part, which is all the cards between the two jokers, including the jokers; and the bottom part, which is all the cards below the bottom joker. Swap the top part with the bottom part. Do not worry if either part is empty:
Before 1 2 A 3 4 5 6 7 8 9 B 10 11 12 13 After 10 11 12 13 A 3 4 5 6 7 8 9 B 1 2 Before 1 2 3 4 B 5 6 7 8 9 10 11 12 13 A After B 5 6 7 8 9 10 11 12 13 A 1 2 3 4 Do a count cut, as follows. Look at the bottom card. Work out the number that it is associated with. Take that number of cards from the top of the pack and place them just above the bottom card. If the bottom card is a joker, then do nothing:
Before 5 6 7 8 9 A 10 11 12 13 1 B 2 3 4 After 9 A 10 11 12 13 1 B 2 3 5 6 7 8 4 Before 1 2 3 A 4 5 6 7 8 9 10 11 12 13 B After 1 2 3 A 4 5 6 7 8 9 10 11 12 13 B Find the output card, as follows. Look at the top card. Work out the number that it is associated with. Count that many cards further into the pack. The card that you reach is the output card. If the top card is a joker, then the output card is the bottom card. Do not move any of the cards:
Before 3 4 5 6 A B 7 8 9 10 11 12 13 1 2 After 3 4 5 6 A B 7 8 9 10 11 12 13 1 2 Before A 2 3 4 5 6 7 8 B 9 10 11 12 13 1 After A 2 3 4 5 6 7 8 B 9 10 11 12 13 1 Unless the output card is a joker, work out the number that is associated with it. This is the next keystream number. If the output card is a joker, then repeat steps 1–5 until they produce a card which is not a joker.
To generate a whole keystream, repeat steps 1–5 until you have enough numbers. It is necessary to keep going until the keystream is as long as the plaintext.
The Solitaire cipher resembles the Vignère cipher. The Vignère cipher is a polyalphabetic substitution cipher. For each plaintext letter, it uses a letter in a keyword to select one of the 26 possible Caesar shift alphabets. Then it uses this alphabet to encipher the letter. But enciphering a letter with a Caesar shift alphabet is equivalent to finding a replacement for the letter by stepping a fixed number of places away from it in the alphabet. Hence the Vignère cipher uses the letters in a keyword in the same way that the Solitaire cipher uses the numbers in a keystream.
There are two main differences between the ciphers. Firstly, the key used in a Vignère cipher is usually a recognisable word or phrase. The keystream used in a Solitaire cipher is not. Secondly, the key used in a Vignère cipher is usually much shorter than the text to be enciphered. This means that each letter in the keyword has to be used to encipher many letters in the plaintext. Moreover, these letters are a fixed distance apart. It follows the number of steps taken in the alphabet to encipher successive letters in the plaintext follows a repeating pattern. With a Solitaire cipher, there is no repeating pattern.
Example
Suppose that you wanted to encipher the text
the moment echo saw narcissus she was in love. she followed him like a starving wolf following a stag too strong to be tackled.
The first step is to choose an initial order for the pack of cards. There are several ways to do this. A standard procedure is the following. You begin with the cards in their natural order (1, 2, 3, 4, …, 51, 52, A, B). Then you use a keyword to shuffle the cards. Each letter in the keyword governs a single round of shuffling. There are 5 steps in each round. The first 4 steps are the ones used to generate keystream numbers. The fifth one is different:
Find the A joker and move it 1 card down.
Find the B joker and move it 2 cards down.
Do a triple cut.
Do a count cut, based on the bottom card in the pack.
Do another count cut, as follows. Work out the position of the current keyword letter within the alphabet:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 Then take this number of cards from the top of the pack and place them just above the bottom card.
Suppose that we use the keyword
SOLITAIRE
The cards begin in their natural order:
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B |
The first round of shuffling, using the letter 'S', causes the following changes:
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B |
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | B | A |
| 1 | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | B | A |
| 1 | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A |
| 1 | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A |
| B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | 1 |
Cipher Solver Tool
| B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | 1 |
| 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 1 |
| 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 1 |
| 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 1 |
(The letter 'S' is the 19th letter in the alphabet. That is why, in step 5, 19 cards are moved.)
So the cards end up in this order:
| 21 | 22 | 23 | … | 49 | 50 | 51 | 52 | A | B | 2 | 3 | 4 | … | 17 | 18 | 19 | 20 | 1 |
After the second round of shuffling, which uses the letter 'O', the cards end up in this order:
Cipher Solving Tools
| 17 | 18 | 19 | 20 | 1 | A | 2 | B | 21 | 22 | … | 50 | 51 | 3 | 4 | … | 15 | 16 | 52 |
Cipher Solver Tools Download
After all 9 rounds of shuffling, this is the order of the cards:
49 50 51 3 4 5 6 7 8 18 11 12 13 14 17 52 19 37 A 44 45 27 28 15 16 9 10 B 20 1 23 24 25 26 22 29 30 31 32 33 34 35 36 2 39 40 41 42 43 21 46 47 48 38
This section is unfinished.
Substitution Cipher Solver Tool
Recognition
Substitution Cipher Solver Tool
There is no sensible way to tell that a Solitaire cipher has been used to encipher a message. The ciphertext will resemble a stream of random letters. Each letter will occur with approximately the same frequency and there will be no significant repetitions of letters or combinations of letters.

